I recently wrote an article about IT request management over at the CloudExpo Journal, part of which discussed the importance of managing and approving user access requests to maintain access control. In addition, I’ve written here about the perils of having a poor offboarding process, leaving transferred or separated employees with the access they should no longer have.
Today InformationWeek published a piece about the hidden risk of privileged user access based on a survey by Ponemon. Clearly, the need for IT governance and better, consistent, and automated ways of dealing with user access requests is on the rise.
Some relevant notes from the survey:
-
One of the primary reasons for employees to have privileged access when they shouldn’t is because of “the IT organization failing to revoke these rights when these employees changed their position.”
-
The problem is getting worse, with “61% of respondents saying they struggle to keep pace with the number of access change requests that come in on a regular basis, up from 53% in 2011.”
-
“58% of IT operations and security managers believe their organizations are unnecessarily granting access to individuals beyond their roles or responsibilities.”
This all leads us back to the importance of using a request management system to capture, route, approve, re-certify, and audit user access requests. As companies grow larger and continue to move faster it’s easy for access to critical systems to be granted improperly.
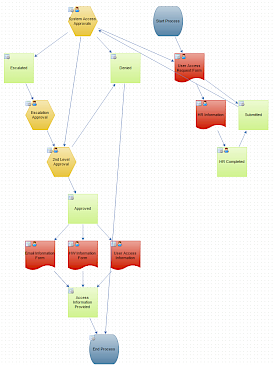
Below is a simple automated workflow for handling system access requests. A form is completed by the requester and the approval process starts. HR confirms the employee’s role and then IT runs the user through two levels of approval, ensuring everyone is in the loop and the access is granted at the highest required level.
This could be a simple, single access request process or it could be part of a larger series of workflows based on the user, the department, the specific access requested, etc. All the information collected and approvals/denials are captured and time-stamped for auditing later.
If you’re responsible for managing access requests and approvals but haven’t implemented any formal request process, this graphic probably has your mind running a bit about what you could be doing with your process. And at some point, you’ll need to start looking at request management solutions. Here’s what people generally look for:
-
Flexible approval management that includes both business and technical owners
-
Self-Generating audit trails that address any compliance requirements
-
Easily traceable process for de-provisioning on employee changes or off-boarding.
-
Visibility for data owners to review access rosters by system, function, geography, etc. (e.g. I own system ABC. Who has access? Are they still an employee? The access roster report).