A lot of firms and Government bodies are reluctant to transfer their SharePoint farms from on premise to office 365 even though the benefits and cost of running SharePoint online outweighs that of an On-premise solution. The main concern of the decision makers is the security of their documents in the cloud. This blog looks into some of the security features provided by office 365 to make sure the data stored in the Microsoft cloud is secured.

Physical Layer
The physical layer involves the security of the data centers which includes access to the buildings and computers through a network or direct access.
The facility
-
Physical access control uses multiple authentication.
-
Security processes including badges, smart cards, biometric scanners, on-premises security officers and continuous video surveillance
-
Two-factor authentication, two factor authentication is when a user has to use two different artifacts to prove they are authorized to have access. An example of the two factor authentication is the ATM machine where the user needs a card and a pin number to prove themselves.
The Network
-
The servers only allows the minimum numbers of ports, protocols and connections that are needed for the server to run smoothly to be open, all the other points of access are blocked to prevent intrusions through these ports.
-
Access Control Lists (ACLs), IPsec policies on hosts, firewall rules and host based firewall rules are implemented in the network with restrictions on network communication, protocols, and port numbers.
-
The networks on the backend are also segregated and separated on a physical level, so that even the security is breached in one server the attacker won’t have access to the whole network.
Logical Layer
This layer includes processes that secures a server from applications running on the host machines to the administrators using the host machine. Below is a list of some of processes used to implement security in the logical layer.
-
Automated Processes: The use of automated processes limits human access to the host machine which reduces the risk of human error and any infringement on sensitive resources on the host machine by a human being.
-
Administrator access to data: Due to the automated processes, Microsoft engineers will have very little interaction with user data, office 365 have just implemented a security feature called “ Customer Lockbox” with this feature, Microsoft will send a request to the user for permission to access the user’s data.
-
Role Based Authentication: ensure that there are appropriate background checks and strict account management so that only those essential to the task may perform the task.
-
SDL : The Security Development lifecycle is a set of practices and techniques that Microsoft uses to develop office 365 applications, this implies that security is one of the most important factors when developing office 365 applications.
-
-
Help prevent malicious software (malware) and unsupported applications from affecting computers in your environment.
-
Prevent users from installing and using unauthorized applications.
-
Implement application control policy to satisfy portions of your security policy or compliance requirements in your organization.
-
Data Layer
-
Office 365 services follow industry cryptographic standards such as SSL/TLS (Secure Sockets Layer / Transport Layer Security), AES etc. to protect confidentiality and integrity of data.
-
Microsoft is working to support and deploy strong encryption using SSLv3.0 support and TLSv1.1/1.2 across all workloads. The use of TLS/SSL establishes a highly secure client-to-server connection to help provide data confidentiality and integrity between the desktop and the data center.
-
Bit Locker is used to encrypt any file that is saved in office 365.
-
Office 365 moves beyond a single encryption key per disk to deliver a unique encryption key per file. With this technology, every file stored in SharePoint Online, including OneDrive for Business folders, is encrypted with its own key, and subsequent updates to the file are encrypted with their own unique key as well.
-
Your organization’s files will be distributed across multiple Microsoft Azure Storage containers, each with separate credentials, rather than storing them all in a single database. By spreading encrypted files across storage locations, encrypting the map of file locations itself, and physically separating master encryption keys from both content.

Office 365 Best Security Practices
Sharing Content with external users
One of the advantages of office 365 is the ease at which you can share content with external users that are not in your organization, this could be for marketing reasons or customer support. In this section we will take a look at the best practices for sharing contents.
Sharing sites
-
If you’ve shared an entire site with a user, the user will have access to the entire site depending on the user group, the user will also have access to personal information about users using the People Picker. External users will also appear in the People Picker as site users. As a result their permissions can mistakenly get elevated by another site user.
-
Similarly if you share a team site with an external user the user will have access to that site and all the sub sites in the team site. The best thing to do is to create a sub site with unique permissions and share it with the external user. This approach should be used for One Drive for business to. The trick is to make sure that the external user do not see more they are supposed to, so you will have to be careful when sharing sites. Note: There are a tools you can use to keep an eye on your SharePoint farms, one example is Aquaforest CheckPoint. Checkpoint allows a user to create different types on reports that can be generated at time intervals based on a schedule. You can use this tool to generate reports on the security of your SharePoint Farms.
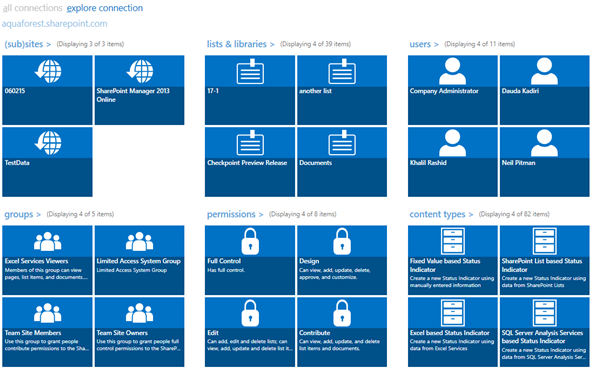
Figure: Checkpoint showing the users of Aquaforest.sharepoint.com
Sharing Documents
If you share documents with anonymous guest links, this means that anyone with access to the link can view the document. This is fine if the document does not contain sensitive information, but if the document is sensitive, you should share it by requiring sign-in instead.
Groups vs Users
When giving permissions to contents in office 365, it is always best to assign it to groups rather than users, this is a good practice because if a user gets transferred to another department within the same company the only thing need to be done is to change the user’s group.
Permission Inheritance
By default office 365 provides a feature called permission inheritance. This means descendants inherits the permission of its parent. This feature makes life easy for the administrator when setting up sites with multiple descendants. This allows them to set the permissions once and apply to all the descendants. Any SharePoint object can be a parent or a descendant. This becomes a problem if some sites contain sensitive information, in this case it is always best to break the permission inheritance so that the sub site will have different set of permissions from the parents. It is also wise to group site with sensitive information into different departments and assign a parent for each group so that the other descendants can inherit from it.
Microsoft Rights Management
Imagine a scenario where you share a document or email with someone and that resource gets sent or shared with a wrong person. Fortunately, with Rights Management in Office 365, you can secure your information and apply an intelligent policy so that only specified internal and/or external people can “act” on your information. With rights access management you can set the following rules on your content:
-
Do not forward (email).
-
Restricted Access (Office apps).
-
CompanyName Confidential: Only people inside your organization (that is, people with an Office 365 account @companyname.com) can access the content, make edits, and share with others inside your company.