Retracing R8 obfuscated stack traces
This guide is for retracing Java stack traces that have been obfuscated with R8 and our ProGuard configuration. These traces often look something like this:
java.lang.RuntimeExceptionPreviewV3Activityjava.nio.charset.MalformedInputException: Input length = 1Oct 3rd 2023, 09:53:55 UTC
STACKTRACE
java.lang.RuntimeException: java.nio.charset.MalformedInputException: Input length = 1 at com.pspdfkit.internal.cu.c(cu:29) at com.pspdfkit.internal.p1.v(p1:1) at com.pspdfkit.internal.b1.a(b1:419) at com.pspdfkit.internal.s1.a(s1:120) at com.pspdfkit.internal.u1.a(u1:364) at com.pspdfkit.internal.u1.getAnnotations(u1:75) at com.pspdfkit.internal.u1.b(u1:61)...
Caused by: java.nio.charset.MalformedInputException: Input length = 1 at java.nio.charset.CoderResult.throwException(CoderResult.java:281) at com.pspdfkit.internal.cu.c(cu:22) at com.pspdfkit.internal.p1.v(p1:1)...
THREADS
Thread 2 - main at android.content.res.AssetManager.getResourceValue(AssetManager.java:504) at android.content.res.ResourcesImpl.getValue(ResourcesImpl.java:233) at android.content.res.Resources.getBoolean(Resources.java:1089) at com.android.internal.policy.DecorView.calculateNavigationBarColor(DecorView.java:1323) at com.android.internal.policy.DecorView.updateColorViews(DecorView.java:1168)...
Thread xxx - etcThread etcetcFor NDK stack traces from our core C++ library, see the NDK crash reports guide.
Our ProGuard configuration obfuscates the code in our internal package, so if it crashes in there, it’s hard for us to determine the source.
We share the ProGuard mapping file for a certain release on request. Contact us at support@nutrient.io to get it. You can also open a support ticket with the crash trace and the version number and we can deobfuscate it. If you want to do it yourself, follow the steps below.
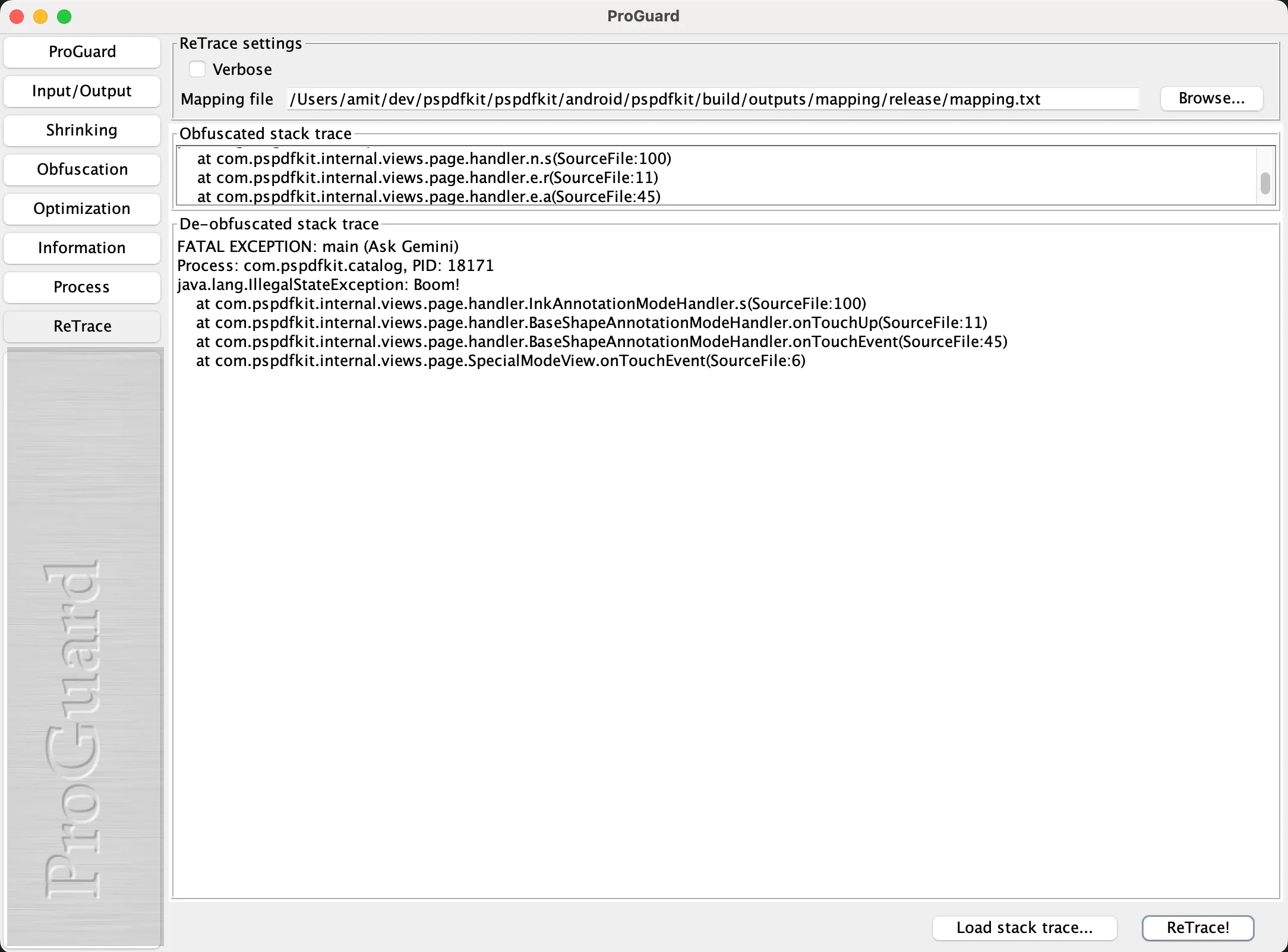
Run the
proguardgui.shapp shipped with the Android SDK. On Mac, it’s usually here:~/Library/Android/sdk/tools/proguard/bin/proguardgui.shClick the ReTrace button.
Paste the obfuscated trace in the Obfuscated stack trace box.
Add the mapping file using the Browse... button or by adding the path directly in the box.
Click ReTrace!
You’ll now see the obfuscated functions, and you can share this with our Support team.
The image below shows what the ProGuard window looks like.