Inspecting APK Files
Table of contents

This article presents the basics of Android reverse engineering. One of the most useful applications of these techniques is reverse engineering your own apps to assess how hard it would be to misuse your private code (for example, getting around your license checks). Another useful application is learning how a certain app solves some interesting technical issue or works around platform or vendor bugs.
Note that the information in this article is not intended for piracy or other illegal uses. Its main purpose is showing how to inspect existing Android apps for educational purposes only.
What Are APK Files?
Android applications are distributed as APK files. APK files are basically ZIP(opens in a new tab) files similar to the JAR(opens in a new tab) files used to package Java libraries. An APK file contains app code in the DEX(opens in a new tab) file format, native libraries, resources, assets, etc. It must be digitally signed with a certificate to allow installation on an Android device.
APK Package Contents
An APK file is a compressed package that contains the following files and directories:
assets— directory with application assets.res— directory with all resources that are not compiled intoresources.arsc. These are all resources except the files inres/values. All XML resources are converted to binary XML(opens in a new tab), and all.pngfiles are optimized (crunched) to save space and improve runtime performance when inflating these files.lib— directory with compiled native libraries used by your app. Contains multiple directories — one for each supported CPU architecture (ABI).META-INF— directory with APK metadata, such as its signature.AndroidManifest.xml— application manifest in the binary XML(opens in a new tab) file format. This contains application metadata — for example, its name, version, permissions, etc.classes.dex— file with app code in the Dex(opens in a new tab) file format. There can be additional .dex files (namedclasses2.dex, etc.) when the application uses multidex(opens in a new tab).resources.arsc— file with precompiled resources, such as strings, colors, or styles.
APK Build Process
The Android app’s build process is fairly complex. Let’s dive into it for a bit so you can get a high-level understanding of how the APK is produced.
- The process starts with the application’s source code in Java/Kotlin, along with its dependencies. First, this source code is compiled to Java bytecode using Java/Kotlin compilers. Note that the application’s dependencies are already compiled and require no additional processing in this step. These include both Android dependencies shipped as AAR(opens in a new tab) files and Java-only dependencies in the form of JAR(opens in a new tab) files.
- Java bytecode produced in the previous step together with all the dependencies is then converted into Dex(opens in a new tab) files containing Dalvik bytecode(opens in a new tab) that can run on Android devices. This produces the
classes.dexfile (or multipleclasses*.dexfiles if multidex(opens in a new tab) is enabled). - Application resources are compiled with the Android Asset Packaging Tool(opens in a new tab). This tool processes all resources into a binary format optimized for Android use. Its output is an APK file with all resources except code — i.e. the
assetsandresdirectories, theresources.arscfile with precompiled resources, and the application’s manifest. - The compiled application code with all the
classes.dexfiles produced in step 2 and the native libraries are packaged into the APK file. - The APK file is then optimized with zipalign(opens in a new tab). This step ensures that all uncompressed data in the APK file is aligned to a four-byte boundary to improve runtime performance when accessing large binary data such as images.
- Finally, the APK file is digitally signed so it can be verified and installed on any Android device.
The final APK file can be used for testing (debug builds) or released into the wild, either through a distribution platform such as Google Play, or as a standalone APK package that can be sideloaded by users.
APK Inspection
Now you have some basic understanding of the APK file format and we can get started analyzing these files.
Note: The APK of PSPDFKit’s PDF Viewer(opens in a new tab) with the package name
com.pspdfkit.vieweris going to be used in all examples below.
Before we can start inspecting APK files, we first need to access them. This is straightforward when working with your own apps, as you should already have access to their APKs. Third-party apps can be pulled from any device they are installed on:
adb pull `adb shell pm path 'com.pspdfkit.viewer' | cut -d ':' -f 2` pdf-viewer.apkUnzip
As stated before, an APK is basically a zip file. So we can just use any unzip tool or file browser with support for zip files to look into an APK’s contents. This, however, has a very limited use case:
- We can extract resources and assets that are not processed or are just optimized during the build process. This includes
assets, raw resources (inres/raw), and.pngdrawables (that are optimized but still in the PNG format). - We are not able to get much information from
.dexfiles, as these are binary files. - Reading binary resources (binary XML(opens in a new tab) and
resources.arsc) or a binaryAndroidManifest.xmlisn’t possible.
Android Studio APK Analyzer
The simplest way of decoding the content of an APK is by using Android Studio, which includes an APK Analyzer(opens in a new tab) tool that provides a comprehensive set of tools for analyzing APK files with a matching UI. The APK Analyzer can be invoked by:
- Dragging and dropping the APK into the Android Studio window.
- Selecting the APK via the Build > Analyze APK menu item.
File Browser
The APK Analyzer provides the files browser with file sizes and their relative percentage of the entire APK size. This feature is useful in identifying the biggest parts of your app when optimizing its size.
Binary Resources Decoder
Binary-encoded resources and AndroidManifest.xml are decoded by the APK Analyzer. Having access to the decoded AndroidManifest.xml is especially useful for verifying results of the manifest merger that is used when building multi-module applications.
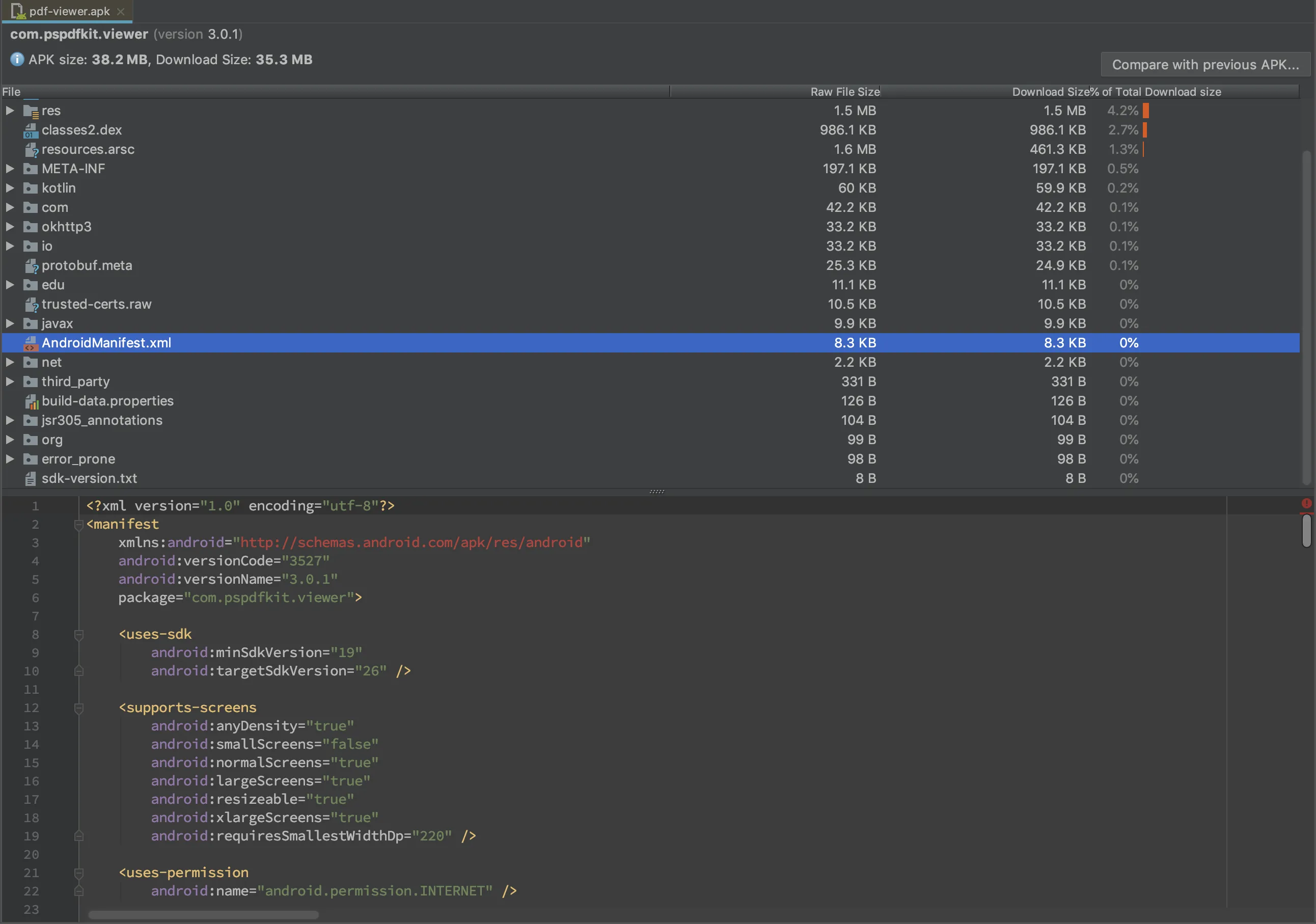
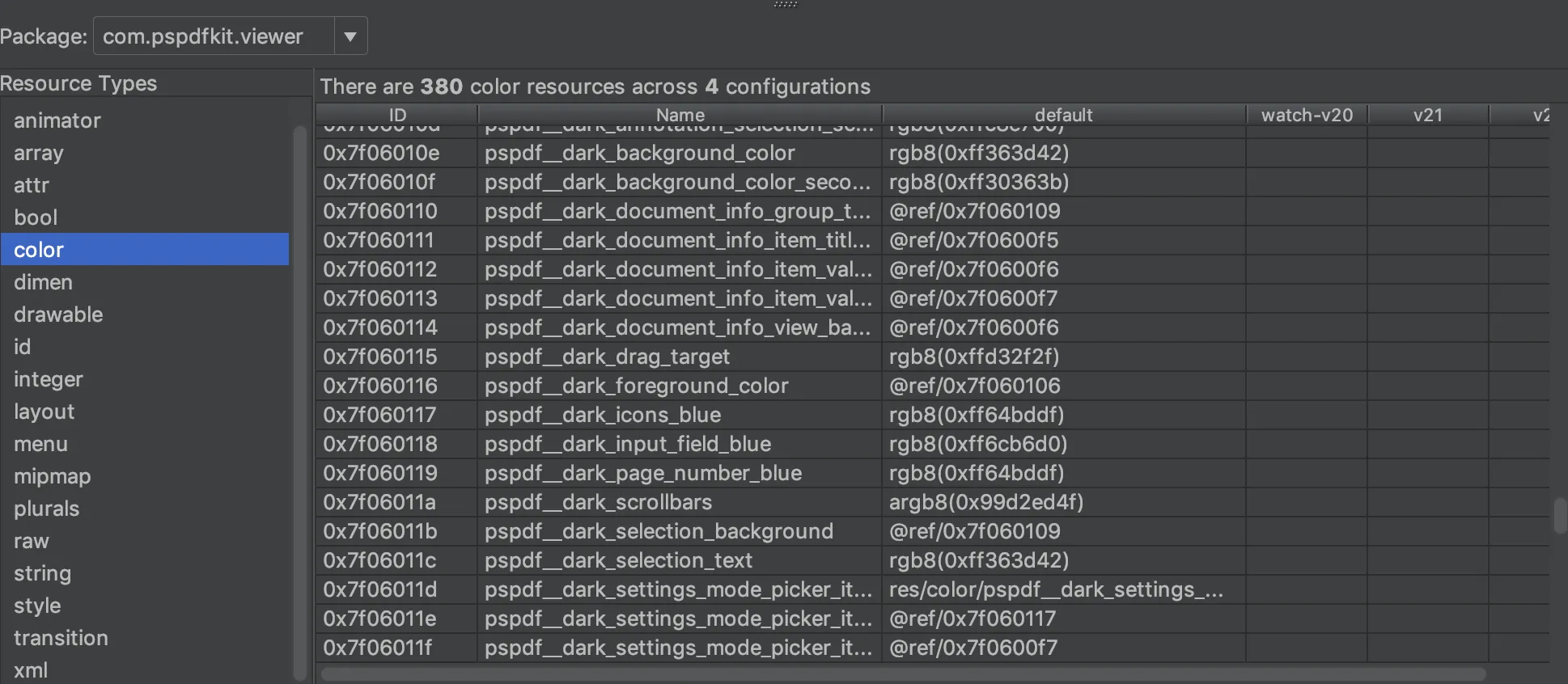
We also get access to decompiled resources that are part of the precompiled resources file (i.e. resources.arsc).
Dex Decoder
The APK Analyzer provides nice support for decoding Dex files.
The most useful feature here is the Referenced Methods column that shows counts for all method references. This information comes in handy when analyzing the number of references in apps in order to stay below the 64K methods limit.
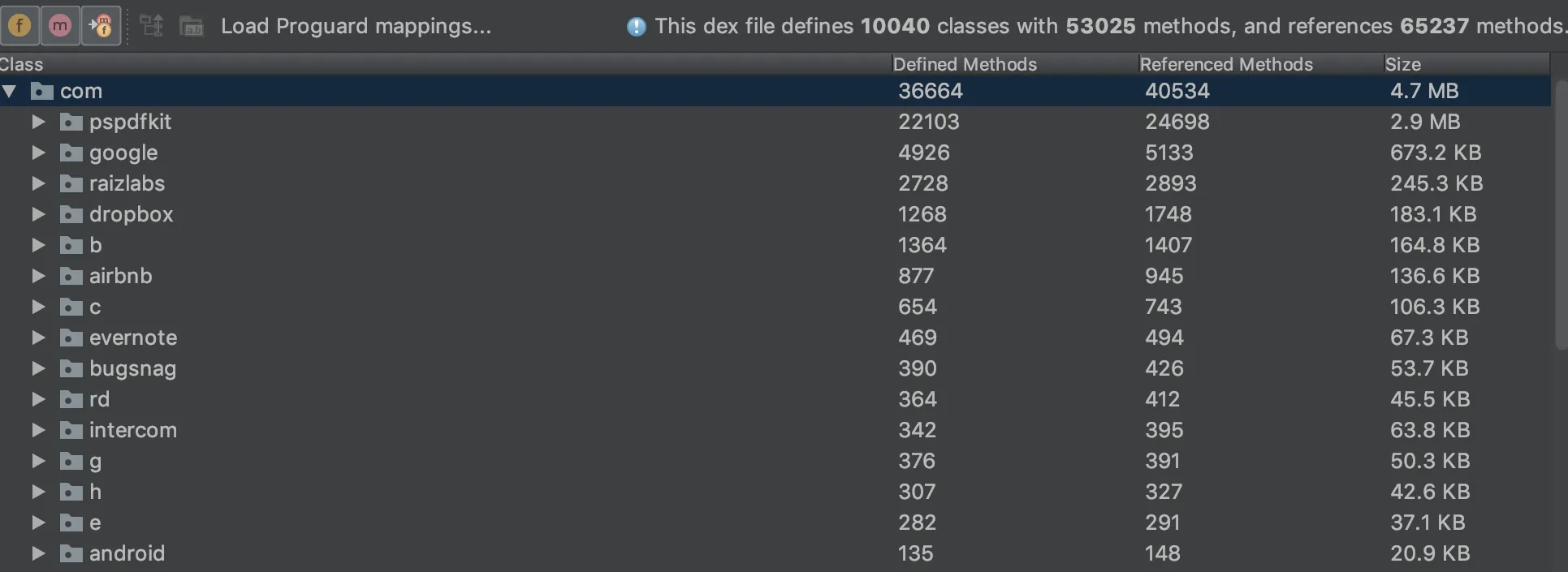
We can navigate through the entire code and search for usage of classes and methods by right-clicking on the class or method names and selecting the Find Usages option. We can also decompile classes and methods into smali bytecode by selecting the Show Bytecode option in the same context menu.
What is smali(opens in a new tab) bytecode, you ask? Well, it’s a disassembler syntax for Dalvik bytecode(opens in a new tab). Its syntax is out of the scope of this article, but we’ll explain how to decompile APKs to more readable Java code further down.
Apktool
Apktool(opens in a new tab) is a comprehensive solution for disassembling Android apps that have more features than the APK Analyzer. It allows for extracting and decoding all files in the APK with a single command:
apktool d pdf-viewer.apkThis produces a directory with decoded resources and a decoded manifest, along with disassembled smali bytecode. The biggest benefit of using Apktool is the ability to edit this disassembled data and build it back into a working APK file. Again, this is outside the scope of this article.
Extracting Java Code
We’ve already seen how to inspect APKs and disassemble Dex files into smali bytecode. There are a few tools that can decompile application code into reasonably clean Java code.
We will use these two tools:
- dex2jar(opens in a new tab) is the suite of tools for working with Android
.dexand Java.classfiles. - Java Decompiler(opens in a new tab) (JD-GUI) is a utility that displays Java source code for
.classor.jarfiles with Java bytecode.
The first step is to convert Dalvik bytecode(opens in a new tab) from our APK into the JAR file with Java bytecode. We’ll use the handy d2j-dex2jar from the dex2jar suite:
d2j-dex2jar -f pdf-viewer.apkThis produces the pdf-viewer.jar file that can be opened directly in the JD-GUI.
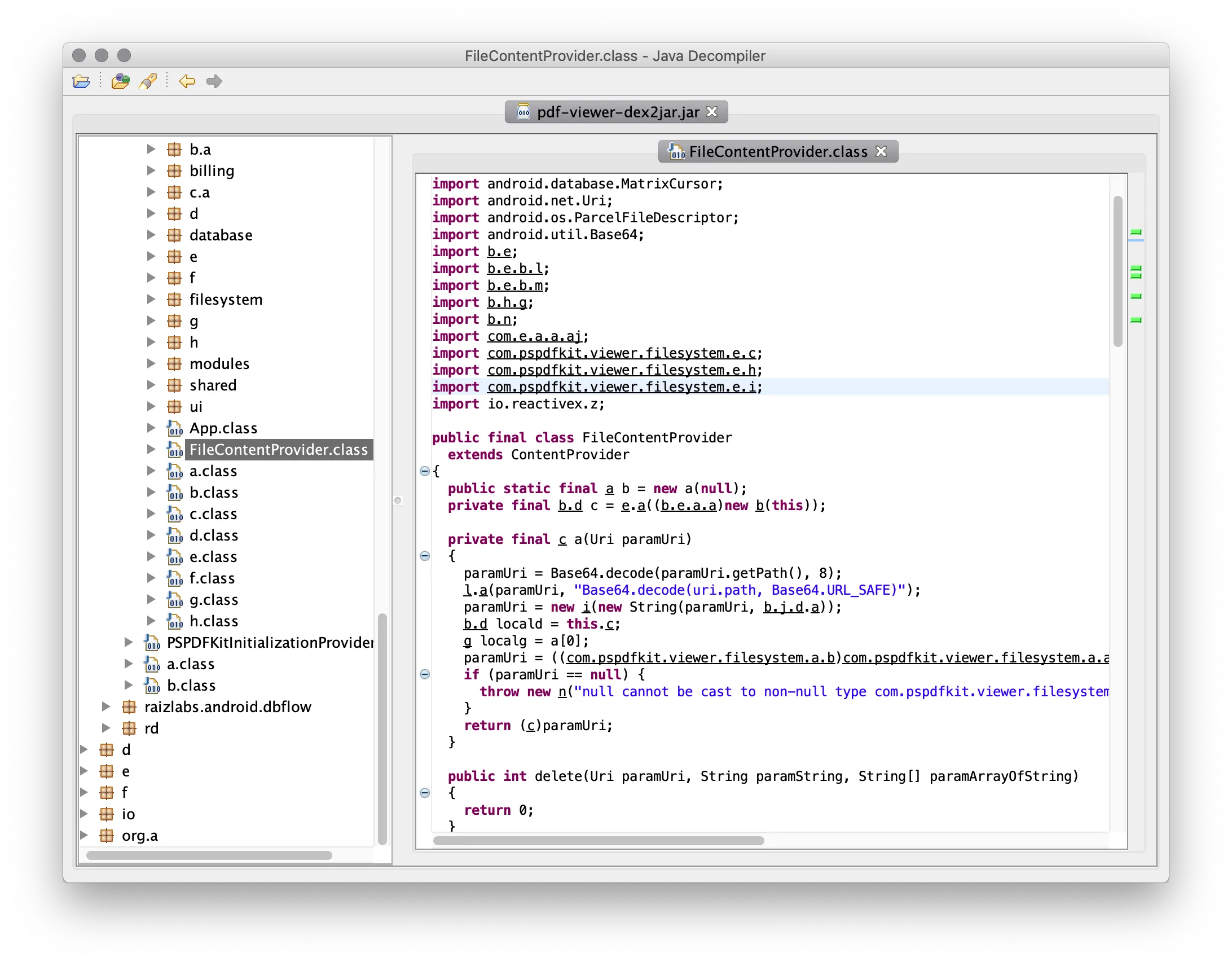
JD-GUI supports basic code navigation — for example, navigating to underlined symbols, searching for symbols by name, and resolving type hierarchy. However, if you miss your favorite editor, you can extract all sources via File > Save All Sources and open them in your editor of choice.
ProGuard
As you can see in the screenshots above, most of the symbols in decompiled code are named with one- or two-letter names. This is the result of obfuscating PDF Viewer’s code with ProGuard(opens in a new tab). This improves speed and makes it slightly more difficult for a potential attacker to navigate through our internal business logic.
Please note that I used the wording “slightly more difficult” in the previous sentence. That’s because ProGuard is hardly enough to warrant security of your application’s private code. Anyone with enough time can understand your code even when using ProGuard. You should never include any business-critical information in your applications, as this can potentially be misused by someone with enough time and knowledge.
Some apps are also using commercial obfuscation solutions, such as DexGuard(opens in a new tab), which make it almost impossible to reverse engineer them. DexGuard performs additional obfuscation steps on top of ProGuard, including runtime encryption of all classes and strings assets. Use these solutions if you want to make your apps safe (in practical terms) from the reverse engineering techniques described in this article.
Conclusion
I hope that the techniques and tools introduced in this article gave you some valuable insight into how easy it is to take most Android apps apart. I also hope that the tools described in this article will become indispensable additions to your Android development toolbelt, allowing you to improve the quality of your apps by providing insight into your production APKs.
FAQ
You can inspect APK files by extracting them with tools like Android Studio, APKTool, or by renaming the .apk to .zip and unzipping it to explore its directories and contents.
An APK file contains code (.dex files), resources (images, layouts), the AndroidManifest.xml file, and other metadata that define the app’s functionalities and permissions.
Inspecting APK files is essential for developers to understand how an app is structured, troubleshoot issues, ensure security, and verify compliance with app store guidelines.
Yes, you can modify APK files, but it requires decompiling the code and resources, making changes, and recompiling them, which can be complex and might affect app functionality.
Recommended tools for inspecting APK files include APKTool for decompiling, JADX for viewing Java code, and Android Studio for analyzing and debugging the app structure.







