PDFium in 2025: Secure, high-performance PDF rendering explained
Table of contents

In 2014, Nutrient forked PDFium — the C++ PDF rendering engine powering Chrome and Edge — to support enterprise document workflows. Our fork maintains security parity with upstream Chromium while adding enterprise-grade features informed by large-scale production deployments across industries.
Rumors persist that open source PDF libraries are inherently insecure or poorly maintained. Yet PDFium(opens in a new tab), the permissively licensed C++ engine embedded in Google Chrome, Microsoft Edge, and hundreds of commercial SDKs renders billions of pages daily across mission-critical systems worldwide.
In this 2025 analysis, Nutrient CEO Jonathan Rhyne separates fact from fiction, examining why enterprise CTOs continue choosing PDFium for their most demanding document workflows.
The PDFium reality: Powering the modern Web
PDFium is more than an open source project, it’s the PDF foundation of the internet. This high-performance C++ library handles PDF rasterization in environments where speed, memory efficiency, and reliability are non-negotiable.
Key Insight: PDFium processes more PDF content daily than any proprietary alternative, benefiting from continuous testing across billions of real-world documents.
Why Nutrient forked PDFium in 2014
Release Control
Enable faster resolution of production issues without waiting for upstream merges, ensuring enterprise SLA compliance.
Capability Extension
Add rendering features and performance optimizations beyond Chromium’s browser-focused use cases.
Over a decade later, our fork continues active development, promptly integrating all upstream security patches while preserving enterprise-specific enhancements that would never be accepted in the browser-focused upstream project.
Myth vs. reality: PDFium security
Myth #1: “Open source means insecure”
Reality: You’re already trusting open source technology daily. Consider the browser statistics:
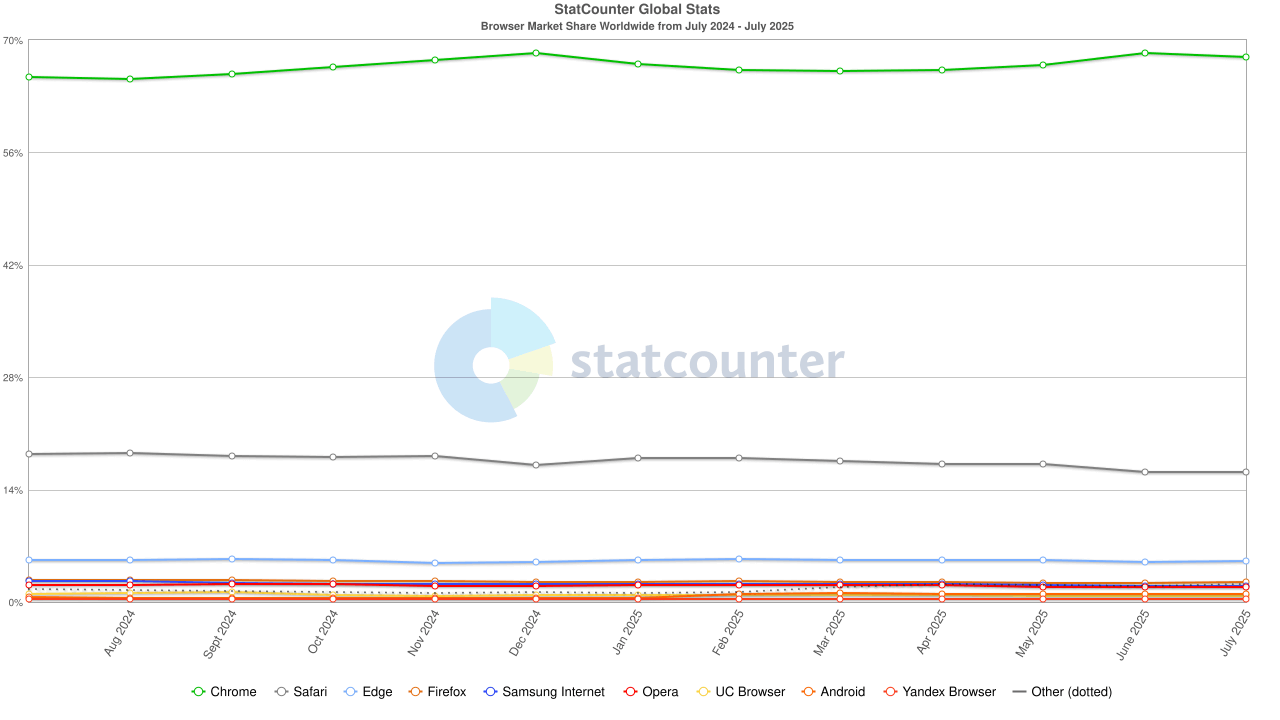
Browser market share worldwide (July 2025): Chrome (67%), Safari, Edge, and Firefox combined represent over 91% of global usage — all either fully open source or embedding open source technology like PDFium.
The Scale: Billions of users rely on open source web browsers daily. If open source were inherently insecure, the modern web couldn’t exist.
Myth #2: “PDFium lacks enterprise security”
Reality: Fortune 500 companies actively contribute to and deploy PDFium:
Google: Powers Chrome’s PDF viewing (billions of daily users) Microsoft: Embedded in Edge browser for Windows 10/11
Amazon: Integrated into Echo and Fire TV products Dropbox: Handles document preview across client applications
These companies wouldn’t stake their reputations on insecure technology. Their continuous contributions create a security review process more rigorous than most proprietary alternatives.
Our enterprise fork: Technical architecture
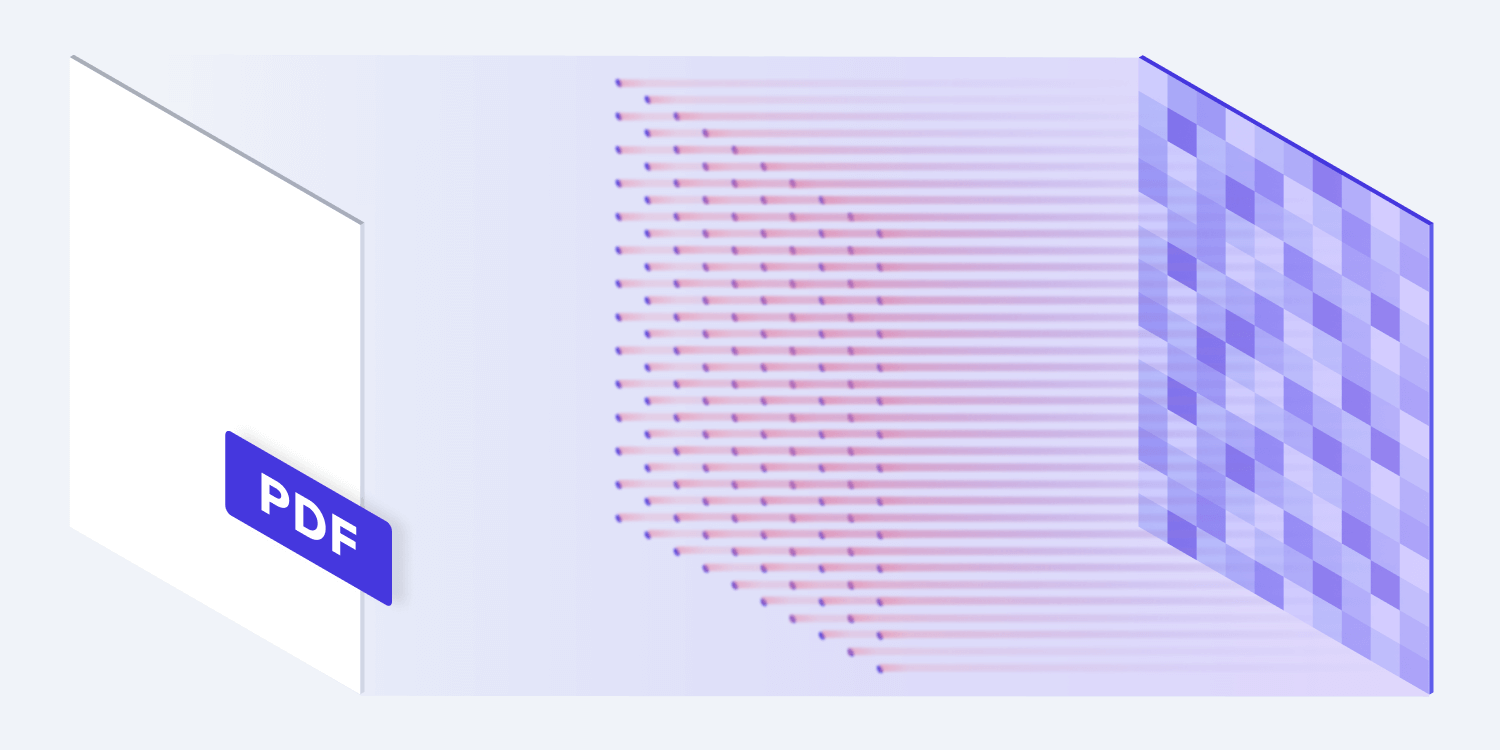
PDF architecture overview: Modern PDF tools separate parsing (reading document structure) from rendering (visual presentation). PDFium excels at the rendering layer while maintaining memory safety and performance.
Security-First development process
Upstream integration strategy:
- Monitor Chromium security advisories and PDFium commits
- Integrate all relevant vulnerability fixes and memory safety improvements
- Validate patches through automated regression testing
- Maintain security parity with Chrome/Edge deployments
Enterprise enhancements:
- Performance at Scale: Threading and memory optimizations for high-volume rendering across iOS, Android, Web Standalone, and server environments
- Text Extraction Improvements: Better accuracy and robustness across diverse document structures
- Production Hardening: Hundreds of fixes for edge cases in malformed documents
Security Advantage: Dual coverage from upstream fuzzing infrastructure plus fork-specific test suites results in lower vulnerability exposure than closed-source alternatives.
Maintenance model: Best of both worlds
Parallel development streams:
- Upstream Syncs: Regular integration of Chromium security and stability patches
- Enterprise Commits: Production-informed enhancements from Nutrient’s engineering team
Validation pipeline:
- Unit tests from both upstream and fork-specific codebases
- Rendering comparison tests using synthetic and real-world PDF corpora
- Performance benchmarks detecting throughput and memory regressions
The enterprise advantage
After more than a decade of active development, Nutrient’s PDFium fork delivers:
- Security parity with Chromium builds through continuous upstream integration
- Extended feature coverage for specialized document workflows beyond browser use cases
- Performance optimizations tuned for both client-side and high-volume server rendering
- Production hardening from billions of pages processed across diverse industries
For teams evaluating PDF solutions in 2025, our fork represents the convergence of browser-grade security with enterprise-grade rendering capability.
The community advantage
“If you want to go FAST, go alone. If you want to go FAR, go together.”
This philosophy drives Nutrient’s participation in the PDFium community. While each company has unique business requirements, we’re collectively committed to advancing PDF technology that benefits everyone.
The result? A PDF rendering platform that’s:
- Battle-tested across billions of daily page views
- Continuously improved by diverse industry needs
- Secured through transparent, collaborative development
- Optimized for both performance and reliability
Conclusion
The evidence speaks clearly: PDFium isn’t just trusted by major technology companies — it’s the foundation of how the world processes PDF content. The question isn’t whether open source PDF technology is secure, but whether you can afford to use anything else.
Enterprise teams choosing PDF solutions in 2025 need battle-tested reliability, transparent security, and proven scalability. Nutrient’s PDFium fork delivers all three.
FAQ
PDFium benefits from continuous security review by major technology companies, transparent vulnerability disclosure, and rapid patch deployment. Proprietary solutions lack this collaborative security model.
We monitor upstream commits and security advisories, selectively cherry-pick relevant patches, and validate integration through automated testing — ensuring our fork maintains the same security posture as Chrome and Edge.
Our fork adds enhanced font handling, PDF/A compliance features, server-optimized threading, and production-hardened edge case handling that wouldn’t be accepted in the browser-focused upstream project.
While you could use upstream PDFium, our fork provides enterprise-specific optimizations, faster issue resolution, and professional support — plus a decade of production-informed improvements.
We continuously monitor upstream changes and integrate security patches promptly. Major feature updates are evaluated based on enterprise needs and compatibility with our enhanced functionality.
Ready to leverage enterprise-grade PDF rendering? Explore how Nutrient’s SDKs deliver PDFium’s power with professional support, advanced features, and production-ready deployment guides.
Sources
- The list of companies that contribute to PDFium, which include Google, Microsoft, and Dropbox(opens in a new tab)
- The list of open source software used by Amazon Echo devices, which includes PDFium(opens in a new tab)
- The Dropbox.Tech blog discussing the performance of PDFium in Dropbox software(opens in a new tab)
- Microsoft Edge uses Chromium, which includes PDFium(opens in a new tab)







